 AntiPolygraph.org has today published a collection of documents associated with the National Center for Credibility Assessment’s training courses on polygraph countermeasures. These documents, which date to circa 2013, describe the U.S. government’s best efforts to detect polygraph countermeasures. Key revelations include:
AntiPolygraph.org has today published a collection of documents associated with the National Center for Credibility Assessment’s training courses on polygraph countermeasures. These documents, which date to circa 2013, describe the U.S. government’s best efforts to detect polygraph countermeasures. Key revelations include:
- In a secret 1995 study, 80 percent of test subjects who were taught polygraph countermeasures succeeded in beating the U.S. government’s primary counterintelligence polygraph screening technique. The training took no more than an hour. NCCA officials have concealed this study from the National Academy of Sciences and the American public;
- The federal government’s methods for attempting to detect polygraph countermeasures are conjectural in nature and were developed by two non-scientist polygraph operators at the federal polygraph school;
- The U.S. government’s polygraph countermeasure detection training is centered on countering information found on two “anti-polygraph websites” (including this one) run by U.S. citizens (one of whom was entrapped and sent to prison and the other of whom was targeted for entrapment). Minimal attention is paid to foreign intelligence services.
The core of the U.S. government’s training for polygraph operators on how to detect countermeasures is a 40-hour “comprehensive” course taught by the National Center for Credibility Assessment’s Threat Assessment and Strategic Support Branch (TASS). The course, called “CE 839,” is restricted to federally certified polygraph operators. The NCCA website, which disappeared from the Internet shortly after the 2016 presidential election, described the course thus (PDD is short for “Psychophysiological Detection of Deception,” a buzzword for “polgyraphy”):
This 40-hour course prepares the PDD examiner to deter and detect employment of polygraph countermeasures in criminal and intelligence testing environments. The course presents background information for a foundation in concepts, theories, and research data related to polygraph countermeasures. Laboratory exercises are included to enhance skills and provide hands-on experience. Detailed discussion of numerous case studies involving examples of confirmed countermeasures. Law enforcement and intelligence PDD examinations are used to demonstrate methods of detecting and defeating this threat. Information provided includes discussion of threats posed by foreign intelligence services, terrorist organizations, and other criminal elements attempting to defeat law enforcement and intelligence PDD examinations. This course is intended as the primary polygraph countermeasures course for criminal and security screening PDD examiners or as a periodic refresher course for examiners supporting intelligence operations. The course included daily directed reading assignments followed by classroom discussions and quizzes.
The documents published today by AntiPolygraph.org include an instructor’s template as well as PowerPoint presentations (including presenter’s notes) for the course.
A note to slide 7 of the first block of instruction (18 MB PDF), dubbed “Back to Basics,” chides AntiPolygraph.org for publishing two Arabic-language jihadist documents on polygraph countermeasures with English translations, averring that “For the Anti-polygraph crowd the ‘end justifies the means’ – they are willing to compromise national security in their quest to rid the world of polygraph.”
No explanation is provided as to how AntiPolygraph.org’s documenting of jihadist literature on polygraph countermeasures (and in the process bringing it to the attention of the federal polygraph community) constitutes our compromising national security. We would counter that NCCA is compromising national security through its embrace of the pseudoscience of polygraphy and its mulish resistance to independent review of its “research” findings.
This “Back to Basics” presentation also includes a suggestion (at slide 22) to overinflate the blood pressure cuff (which causes pain) to punish examinees who breath more slowly than the polygraph operator would like:
 Block 2 (11.4 MB PDF) of the comprehensive course (“Physiological Features”) is what NCCA considers to be the core of the course. It identifies features of polygraph tracings that NCCA believes are indicative of polygraph countermeasure use. Although none of the NCCA documents provided to AntiPolygraph.org are marked as being classified, the presenter’s notes for slide 5 state that the discussion will be classified “secret”:
Block 2 (11.4 MB PDF) of the comprehensive course (“Physiological Features”) is what NCCA considers to be the core of the course. It identifies features of polygraph tracings that NCCA believes are indicative of polygraph countermeasure use. Although none of the NCCA documents provided to AntiPolygraph.org are marked as being classified, the presenter’s notes for slide 5 state that the discussion will be classified “secret”:
 The presenter’s notes for the concluding slide (52) bemoan the fact that “Today we have many performing high level CM. The average person can go on-line and find not only the test technique that will be used in their polygraph but the questions asked.”
The presenter’s notes for the concluding slide (52) bemoan the fact that “Today we have many performing high level CM. The average person can go on-line and find not only the test technique that will be used in their polygraph but the questions asked.”
You are at the right site to find that kind of information.
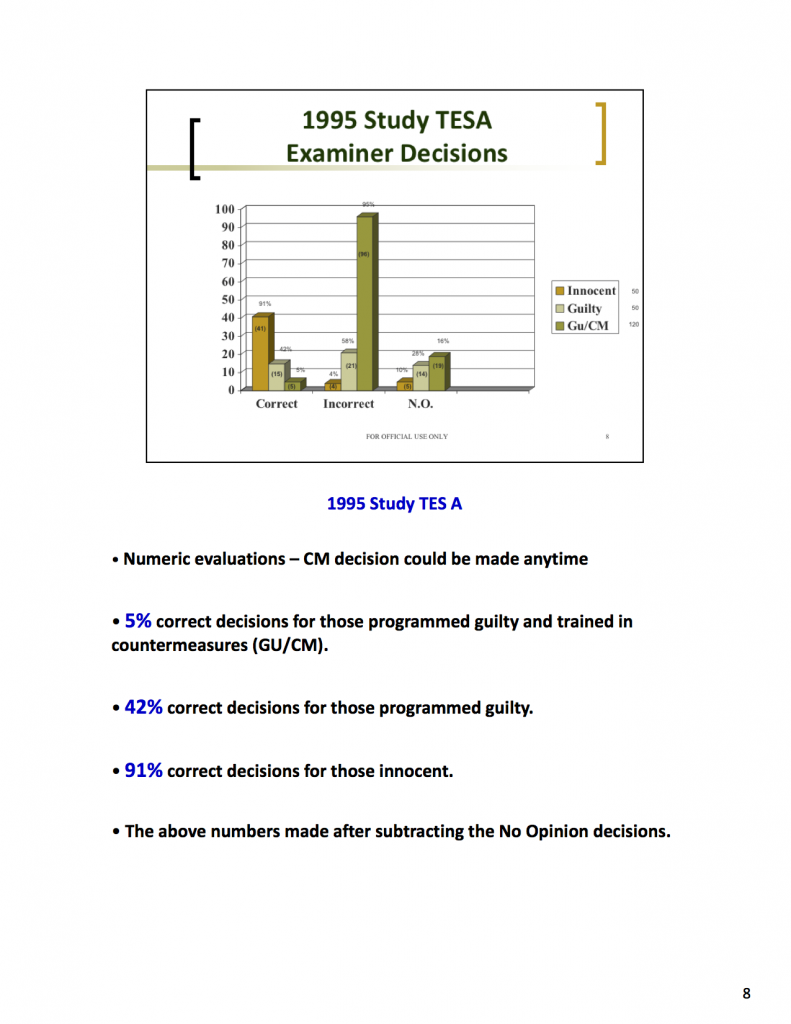
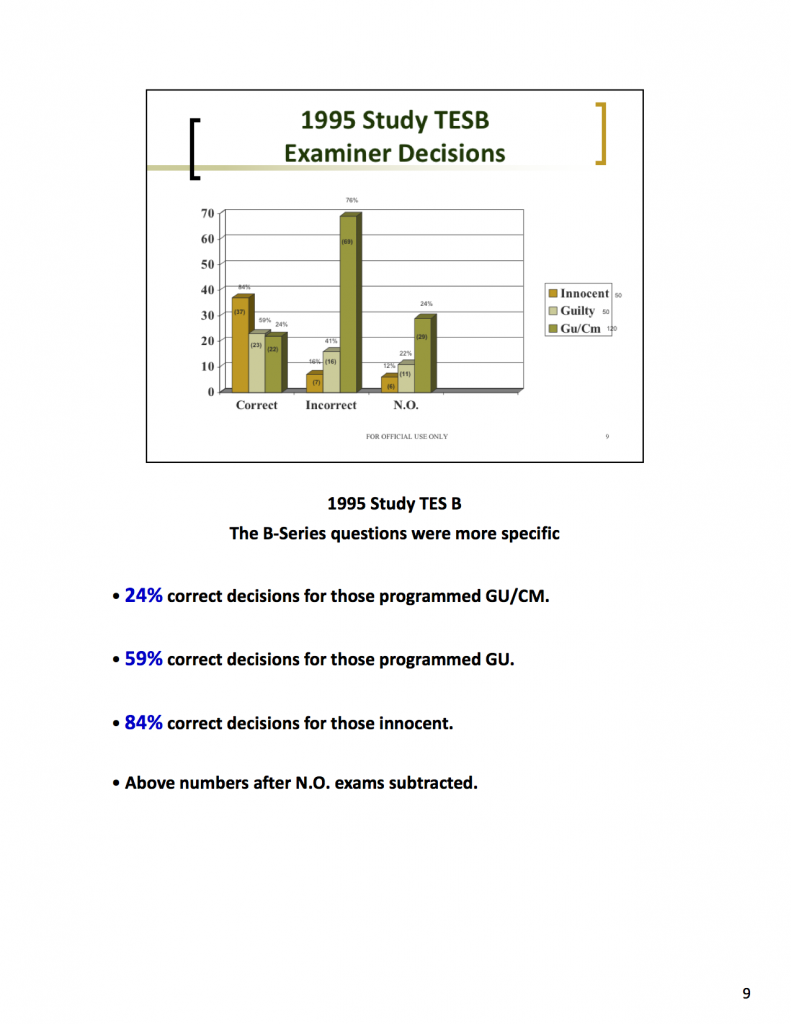
The presentation for the fourth block of instruction (4.5 MB PDF) includes some of the information we found most interesting. It documents a secret U.S. government countermeasure study conducted by Gordon H. Barland circa 1995 in which (including inconclusive results) 80% of test subjects taught to beat the polygraph were successful in doing so. Countermeasure training lasted no more than an hour and consisted of telling the examinee, upon hearing a “control” question, to pick a number over 600 and count backwards by threes.
Slides 7-9, with presenter’s notes, are reproduced below (you can click on the images to view them in a larger size):
Barland’s study strongly suggested that polygraph screening is highly vulnerable to polygraph countermeasures. The U.S. government has concealed this study from the public, including the U.S. National Academy of Sciences’ National Research Council, which in 2001-2002 conducted a review of the scientific evidence on the polygraph. In its report, The Polygraph and Lie Detection (10.3 MB PDF), the Council noted (at p. 118, emphasis added):
“…we were advised by officials from [the Department of Energy] and [the Department of Defense Polygraph Institute, since renamed the National Center for Credibility Assessment] that there was information relevant to our work, classified at the secret level, particularly with regard to polygraph countermeasures. In order to review such information, several committee members and staff obtained national security clearances at the secret level. We were subsequently told by officials of the Central Intelligence Agency and DoDPI that there were no completed studies of polygraph countermeasures at the secret level; we do not know whether there are any such studies at a higher level of classification.”
NCCA deliberately misled, and concealed relevant documentation from, the National Research Council.
With respect to the mention of officials of the Central Intelligence Agency, note that the most influential person at DoDPI/NCCA at the time was Donald J. Krapohl, a career CIA agent and polygraph operator who for many years was the éminence grise at DoDPI/NCCA.
The presentation goes on to document how two non-scientist NCCA staff members, Paul M. Menges and Daniel V. Weatherman, devised a system that purports to identify those who employed countermeasures in Barland’s study by examining the polygraph tracings. Their scheme identifies a number of “physiological features” that are posited to be evidence of polygraph countermeasure use. The criteria are so broad that any polygraph operator could likely find indications of countermeasure use in any particular set of polygraph charts if he looks hard enough. Slide 13 notes that when Weatherman applied his “global scoring” approach to detect countermeasures, only 47% of the innocent were correctly identified.
The entire NCCA comprehensive countermeasure course is centered on these two non-scientists’ unpublished, un-peer-reviewed “research.”
Slide 36 notes: “Software unable to identify CM.” This is not surprising, given the conjectural, “I know them when I see them!” nature of Menges’ and Weatherman’s countermeasure “detection” methods.
It’s worth noting that around the time Menges and Weatherman were attempting to devise a technique for detecting polygraph countermeasures, Menges authored an article published in the American Polygraph Association quarterly, Polygraph, suggesting that teaching polygraph countermeasures to the public should be outlawed.
A decade later, Doug Williams, who runs Polygraph.com, which features prominently in NCCA’s polygraph countermeasure training, was targeted for entrapment in Operation Lie Busters and ultimately sentenced to two years in federal prison. He has since been released but is prohibited from providing in-person training on how to pass a polygraph “test” until July 2020. AntiPolygraph.org co-founder George Maschke was also targeted for entrapment during Operation Lie Busters but was not charged with any crime. Contemporaneous evidence suggests that AntiPolygraph.org was additionally targeted for surveillance by the NSA.
The fifth block of instruction (5.7 MB PDF) covers suggested supplemental polygraph counter-countermeasure techniques such as the “Repeat the Last Word Test,” the “Focused CM Technique,” the “Yes/No Test,” and the abandonment of the “control” question “test” (CQT) in favor of the Concealed Information Test.
On a final note, recall our 11 October 2014 blog post, “Senior Official at Federal Polygraph School Accused of Espionage.” Then recently-retired Defense Intelligence Agency counterintelligence investigator Scott W. Carmichael said this about these documents in an e-mail message to retired FBI polygrapher Robert Drdak:
The study conducted by Dan [Weatherman] and Paul [Menges] drew on raw data collected by Dr. Gordon H. Barland and the classified report of his earlier study of mental countermeasures dated in 1994. Dan, Paul and Dr. Senter performed their work as employees of DoDPI. Your old colleague and former business partner Don Krapohl provided oversight for their work and edited the report submitted by Dan and Paul back in CY2003. The entire effort was official, and it was based on a classified study.
Dan and Paul believed their findings constituted a new, reliable, and therefore extremely valuable diagnostic tool. Dr. Senter tested the tool and determined that, sure enough, the specific diagnostic features identified by Dan and Paul through their study correlated with a high degree of probability to the employment of countermeasures. As you may know, the U.S. government now requires all federal polygraph examiners to receive 40 hours of instruction on polygraph countermeasures to become certified as federal examiners; and, to receive 4 hours of polygraph countermeasures refresher training every year to maintain their certifications. DoDPI/DCCA [sic, correct NCCA] is so confident in the diagnostic tool developed by Dan and Paul, they decided to use the new tool as the very foundation for the 40-hour instruction and the annual 4-hour refresher training.
Again, Dr. Barland’s 1994 study, which formed the basis for Weatherman and Menges’s study, was classified. By definition, then, and by DoD Instruction, Weatherman and Menges’s study and findings, were therefore also classified.
But DoDPI did something stupid. They committed a security violation. In fact, they did so repeatedly. They found it inconvenient and unwieldy to carry classified briefing slides around with them as they traveled to various parts of the country to teach the diagnostic tool to examiners – and, when they found it necessary to brief uncleared personnel on the tool, rather than follow routine but bothersome administrative procedures which would have enabled them to do so, they elected to simply not stamp their briefing slides at all. Instead, they stamped their materials as Unclassified/FOUO – while handling and treating their materials as though they were classified, in order to ensure their tool did not fall into foreign hands. Why? Because anyone who learns how the entire US government now detects the employment of countermeasures, will be able to device [sic] methods to defeat the US government examination process.
Additional NCCA countermeasure training materials, with brief descriptions, are available for download here.


I invented these so-called “countermeasures” in 1979 and gave a detailed explanation of them to the US Congress when I testified in support of the EMPLOYEE POLYGRAPH PROTECTION ACT in 1985. As Dr. Maschke has mentioned in the article above, I was sent to the federal prison for two years for teaching them to an undercover agent. I guess this is what passes for justice in this country nowadays. Sad…
[…] False Confessions is a must-read for students of the history of polygraphy. Doug Williams is indisputably among the most influential persons in polygraphy’s nearly century-long history. His revelation of the polygraph trade’s secrets has earned the wrath of polygraph operators across the United States, and his manual “How to Sting the Polygraph” has long been part of the curriculum for the federal polygraph school’s countermeasures course. […]