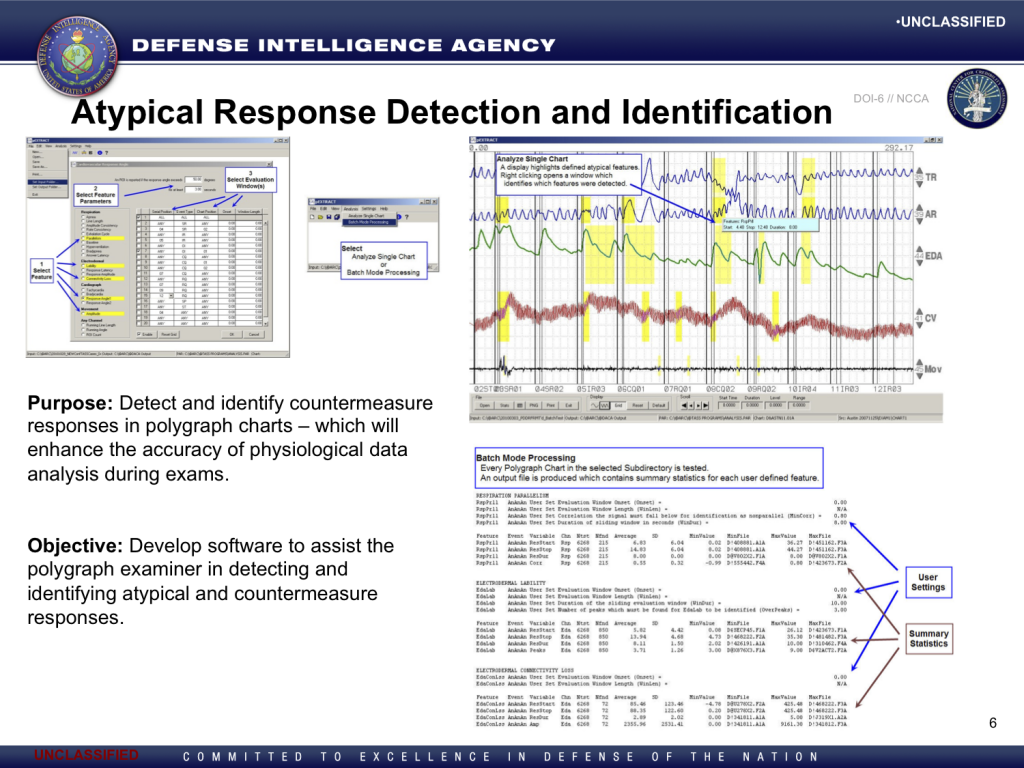
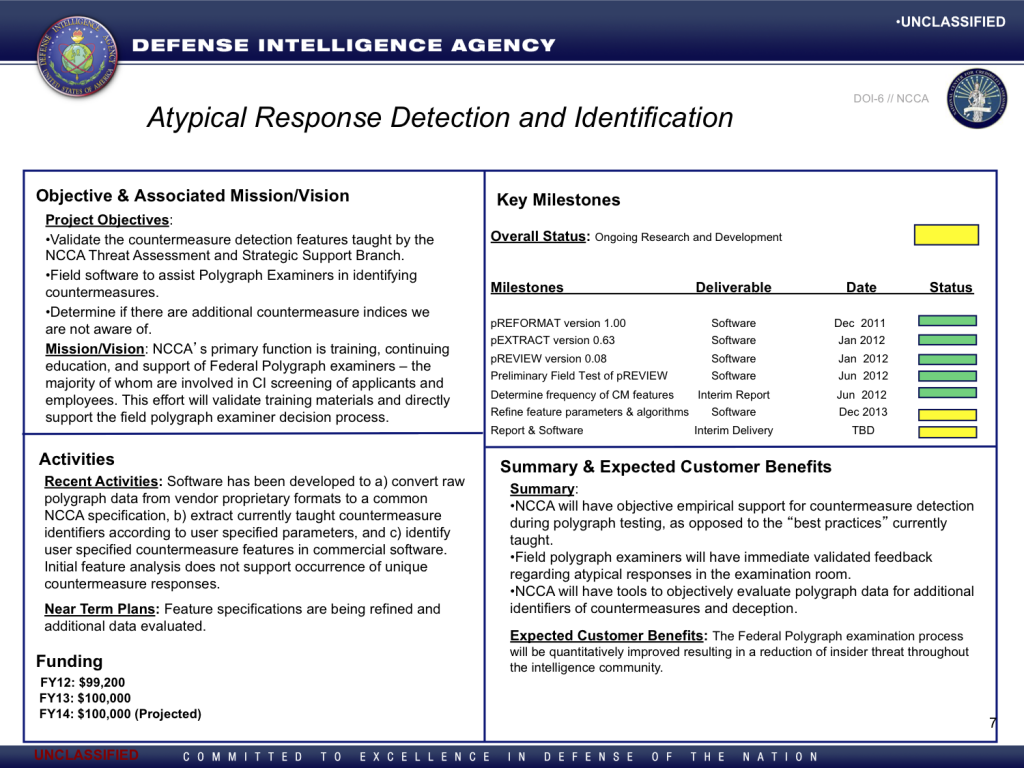
A 2013 presentation by the National Center for Credibility Assessment documents that the federal polygraph school is working on a computer software project intended to automate the detection of polygraph countermeasures. It appears that the software does not employ a new approach to countermeasure detection, but rather seeks to “[v]alidate the countermeasure detection features taught by the NCCA Threat Assessment and Strategic Support Branch.” A competent scientist might first attempt to determine whether such putative “countermeasure detection features” are indeed valid, rather than set out to “validate” them. NCCA seems not to allow for the possibility that any of their teachings might not be valid.
To date, no polygrapher has ever demonstrated any ability to detect the kinds of countermeasures described in AntiPolygraph.org’s free book, The Lie Behind the Lie Detector or in former police polygraphist Doug Williams’ manual, “How to Sting the Polygraph” and documentation obtained by AntiPolygraph.org indicates that the polygraph community has no reliable method of detecting such countermeasures.
Indeed, the federal government considers Doug Williams’ information to be such a threat that it launched a criminal investigation into him, attempted to entrap him and raided his home and office, seized his customer records, and created and distributed a watch list based on them. Williams remains in legal jeopardy for teaching techniques that the head of the U.S. Customs and Border Protection polygraph unit avers “can be routinely identified.”
The NCCA presentation projects that the countermeasures detection software project would be completed by the end of 2013 with a report and software to be delivered at a date that remained to be determined. The project had a budget of $199,200 in fiscal years 2012 and 2013, with another $100,000 projected for fiscal year 2014.
The slides from the presentation that deal with the countermeasure detection software are reproduced below. Among other things, the presentation indicates that NCCA has developed a “common NCCA specification” for polygraph chart data. To AntiPolygraph.org’s knowledge, such specification has not been publicly documented.